Technical updates to underlying architecture and security features are listed below:
Navigation reimplementation (phase 3)
Overview: The updating of the navigation continued to transition frontend pages (ILP) from Angular to React to enable improved design and security. In this update the frontend function pages were updated to allow access by deep links with the consideration of access rights (ACL). This ensures that a page will load empty if the logged user does not have access rights for the navigation.
Benefits and Use Cases: This delivers a more modern experience, secure code, and advanced search initiatives.
Audience: Learners and Managers
Setup & Access: There is a new setting in the design to switch between the old Angular and new React navigation; but the design should first be checked by the imc Design team if required. This settings is available in the Design function by editing a design and checking the Description tab. Activate by ticking the Activate the new navigation checkbox.
Considerations & Limitations: The default value is unticked meaning Angular is used. Only implemented in Kubernetes architecture. Users can access pages via deep link even though they do not have access rights on the Navigation, however the pages will show empty content.
Testing: Check by editing an active design to ensure the Activate the new navigation checkbox is unticked. Tick the checkbox and click the Save button. In a separate browser login and check the learner functions and navigation; if there is an error return the previous browser, untick the checkbox and click Save.
Risk rating: High
New endpoint for IDM to request access tokens
Overview: For clients using the Learning Suite as a headless LMS with own frontend, a new IDM endpoint enables requesting bearer access tokens for users. The user is identified via a SAML request and the response contains the access token.
Benefits and Use Cases: The provided access token can be further used to make multiple API calls in the session. For example, in a headless scenario this simplifies connection and then directly requesting further content such as calling WBT (SCORM) content.
Audience: Technical administrators
Setup & Access: A SAML Configuration with the respective Entity ID is required in advance. A sample of a call to the endpoint is below:
curl --request POST \
--url 'https://customerurl/idm/saml/SSO/alias/mySamlEntityId?grant_type=urn%3Aietf%3Aparams%3Aoauth%3Agrant-type%3Asaml2-bearer&redirect_uri=http%3A%2F%2Flocalhost%3A8080%2Fils&client_id=ILP&client_secret=mySecret' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data 'assertion=PHNhbWxwOlJlc3Bvb......=='
Considerations & Limitations: This is a standard API that requires the Kubernetes architecture and a SAML interface. SAML is a licenced Add-on module.
Testing: Requires an active SAML configuration and calling the POST based on above. If the SAML Response is valid, could be verified, and the user matched; then a valid access token will be returned.
Risk rating: Low
imc Platform Connectivity Service Registry
Overview: A new Service Registry has been developed as a key element of the imc Platform Connectivity (IPC) framework. Microservices are being updated with Arco DSL to be registered on the Service Registry to support DNS discovery by name or ID. The response to a lookup request contains information where to find a web service in a network. In addition to DNS discovery, IPC also supports API discovery, where all services provide resource information that represents the web API endpoints with corresponding request and response type information.
Benefits and Use Cases: Initially the Service Registry will be used by the imc Hosting and Support teams to monitor that ordered micro-services (E.g. Channels, IDM) are active. This enhancement will help imc efficiently ensure all ordered services are functioning as expected.
Audience: imc Support and imc Hosting teams
Setup & Access: Not required
Considerations & Limitations: Part of the imc Hosting service
Testing: Not applicable
Risk rating: Low
Extend Course Preview function
Overview: An update for headless LMS scenarios provides a direct link course preview. The addition of “startPreview=true” to the course.jsf to open the preview of a course.
Example:
https:/yourlms/ilp/pages/course.jsf?courseId=998763&startPreview=true#!/courseroom/course.
The preview will additionally have a Close preview button to close the preview browser tab and clear the cookie session.
Benefits and Use Cases: Administrators who don’t have direct access to the Learning Suite Courses administration function are able to see a preview of the course via direct link.
Audience: Content administrators
Setup & Access: The update is purely implemented for headless scenarios where courses are created in the Learning Suite via API.
Considerations & Limitations: The course preview has the following limitations:
-
Adding of contents via course preview is not possible.
-
Preview is not supported for courses with planning status Cancelled.
The following components are not supported for preview:
-
Collaborative Group Work in OJT is not supported as identification of group is required and is not possible for an administrator/tutor
-
External LTI 1.1
-
External LTI 1.3
-
GoToWebinar
-
Openmeeting
-
Adobe connect recording
-
Vitreo meeting
-
Webex meeting
-
Subcourses
-
AICC WBTs
Testing: Testing is performed via accessing a direct link.
Risk rating: Low
Send course, feedback and test ACL over API
Overview: Previously, there were no APIs to handle clearances for courses, course templates, feedback forms, and tests. New APIs can now handle clearances similar to the recently introduced Media clearances (see image below).
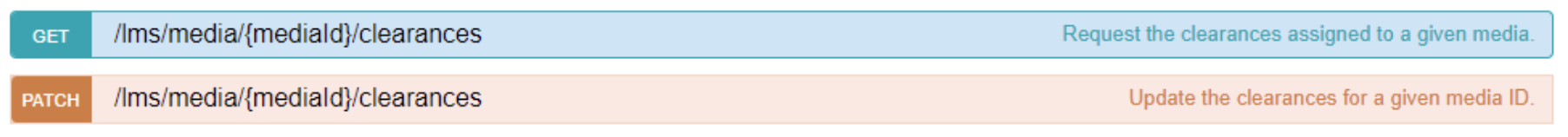
There are REST API calls with Clearances for Courses, Tests, and Feedbacks (working for Tests, Test series, and Feedback forms)
-
GET /lms/tests/{courseId}/clearances
-
PATCH /lms/tests/{courseId}/clearances
-
-
GET /lms/tests/{testId}/clearances
-
PATCH /lms/tests/{testId}/clearances
-
-
GET /lms/feedback/{feedbackId}/clearances
-
PATCH /lms/feedback/{feedbackId}/clearances.
-
Benefits and Use Cases: Customers using RESTful APIs to automate the creation of learning content can now apply clearances. This allows restricting which groups or individual users are able to view and edit the content in the Learning Suite.
Audience: Content administrators
Setup & Access: The response body for the GET method can be used as that for the media clearance API.
Example:
{
"mediaClearanceList": [
{
"objectType": "GROUP",
"objectId": "1",
"name": "Platform Administrator",
"isOwner": "true",
"aclGrantTypes": [
"VERSION",
"EDIT",
"DELETE",
"EXEC",
"NOTIFICATION",
"EDITACL"
]
},
{
"objectType": "USER",
"objectId": "110587",
"name": "Admin, Test 5",
"isOwner": "true",
"aclGrantTypes": [
"VERSION",
"EDIT",
"DELETE",
"EXEC",
"NOTIFICATION",
"EDITACL"
]
}
]
}
The request body for the PATCH method can be same as that for the media clearance API.
Example:
{
"operationList": [
{
"operationType": "ADD",
"objectType": "USER",
"objectId": "701262",
"isOwner": "false",
"aclGrantTypes": [
"EXEC",
"EDIT",
"DELETE",
"EDITACL",
"VERSION",
"NOTIFICATION"
]
},
{
"operationType": "UPDATE",
"objectType": "USER",
"objectId": "701262",
"isOwner": "true"
},
{
"operationType": "DELETE",
"objectType": "USER",
"objectId": "701262"
}
]
}
Considerations & Limitations: Template / type objects, like course types, course templates, test templates, and feedback templates are not considered. It’s also important to note that the create course API returns all the componentId of the course and not the objectId; therefore, the two APIs above support the courseId as the componentId. If additional support is required consider second level support with an imc Technical consultant.
Testing: Requires the use of API to first create content. Then the use of the new APIs to apply clearances to the created content objects.
Risk rating: Low
New API to retrieve PERSON_ID using LOGIN
Overview: A new API endpoint (GET) has been developed to retrieve user PERSON_ID attribute values using the LOGIN attribute values. This supports retrieving an unlimited number of records simultaneously by entering multiple LOGIN values.
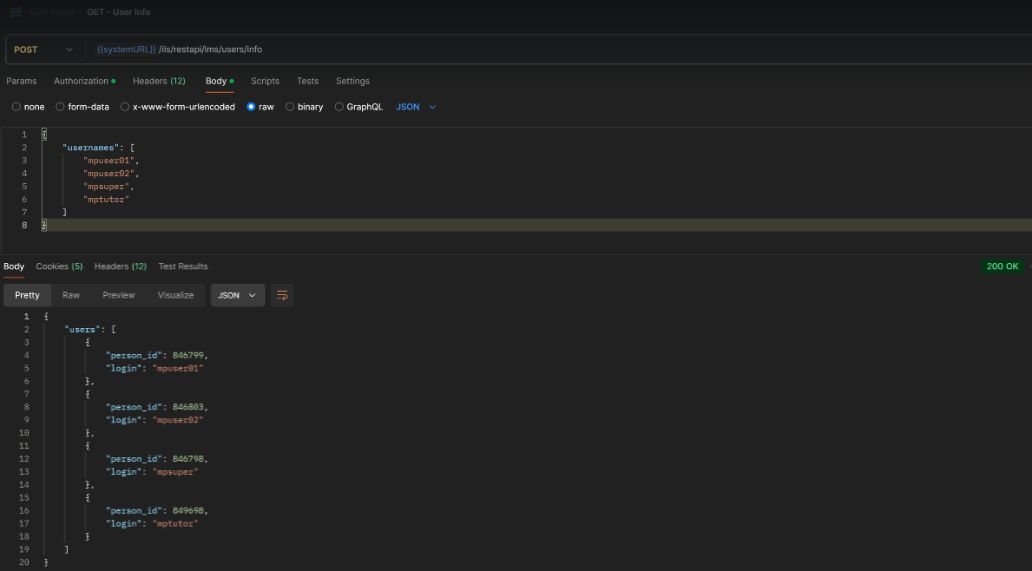
Benefits and Use Cases: Enables external systems to easily extract and store the imc PERSON_ID for each user if the LOGIN is known. This is useful as the PERSON_ID is the personal attribute required by many standard imc APIs to retrieve or update user training data.
Audience: External system administrators
Setup & Access: No setup required
Considerations & Limitations: The endpoint won’t be configurable to other unique user attributes as parameters.
Testing: API request URL:
POST .../lms/users/info
API Request structure:
{
"logins": [
"imc_super",
"imc_admin",
....
]
}
API response structure:
{
"people": [
{
"person_id": 2,
"login": "imc_super"
},
{
"person_id": 1,
"login": "imc_admin"
},
....
]
}
Risk rating: Low
System-wide Updates
Login Page Updates
Overview: An update to the Login page/panel provides the possibility to further add text above SSO and Local login options. The new text fields support both multi-lingual and rich-text input. A further configuration update provides the ability to hide the local login fields behind a new button when SSO is also enabled. To achieve these changes also sees some updates to the location of authentication settings in the Clients function.
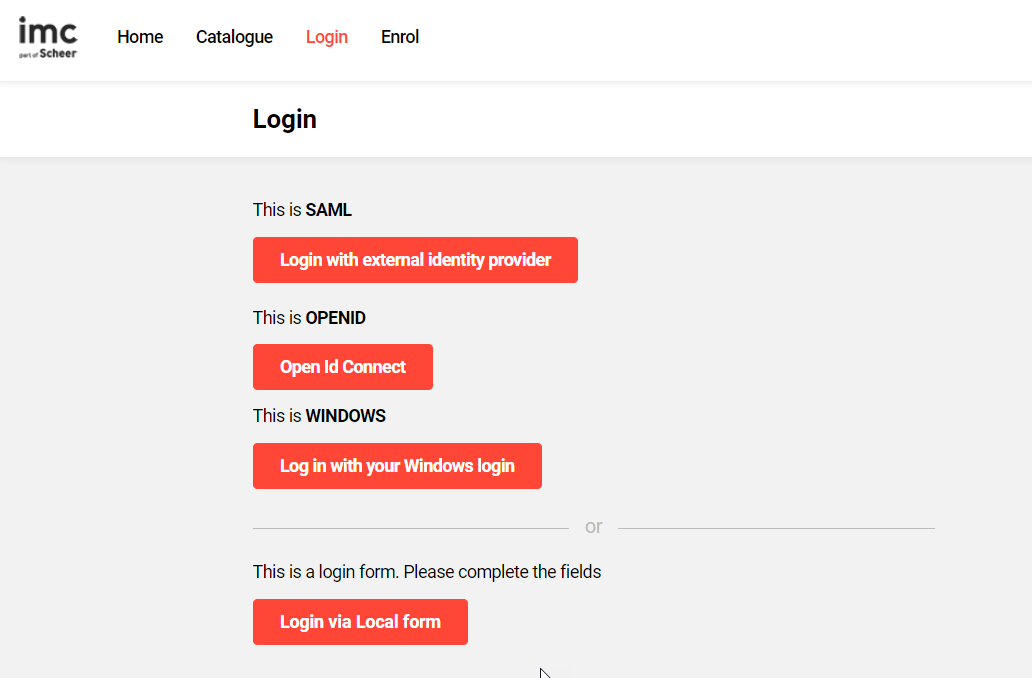
Benefits and Use Cases: The addition of configurable text fields provides a visual distinction and labelling between the different login options. This is ideal for customers that need to support multiple login options within a single client.
Audience: Learners
Setup & Access: In the Clients function there is a new Authentication methods settings tab that is editable per system context. This new authentication method manager:
-
Shows configured authentication methods,
-
Provides an Edit icon with all edit options (no checkbox for enabling at list of methods), and
-
Allows changing the order with arrows.
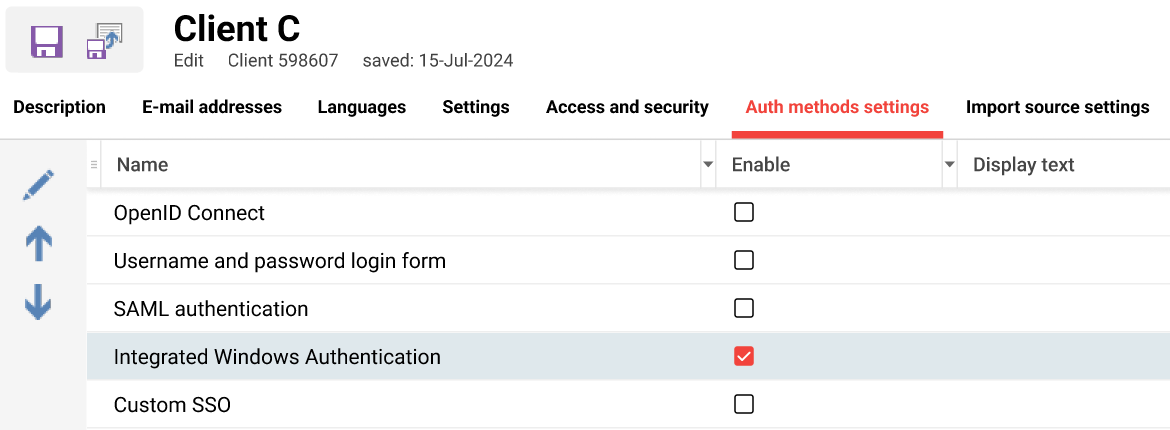
Configuration must be dependent on the system context. The Edit icon will open the Edit manager where the relevant settings for each auth method will be displayed including:
-
A Settings area for the individual authentication configurations.
-
A display text multi-language area:
The languages accepted will be the platform languages.
Note: Text is not inherited from default to option languages if left blank.
Considerations & Limitations: By default the new text fields will be blank and the Local login button unticked to ensure no change.
Testing: As a system administrator, edit a client to check if the new Auth methods settings tab is available. Ensure the enabled authentication methods are correct. Edit the enabled authentication methods to check new settings and language fields.
Risk rating: Low
Meta Tag Refactoring II
Overview: Further updates have occurred on many meta tags to correct assignability, add missing operating instructions (i-button text), and descriptions.
Benefits and Use Cases: This enhancement ensures a more streamlined and meaningful meta-tagging process, reducing the assignment of irrelevant tags significantly. Furthermore, the updated meta tags may not be added where they were not intended to be so that unexpected behavior can be mitigated.
Audience: Administrators
Setup & Access: No configuration required
Considerations & Limitations: Meta tags that were already assigned to courses, learning paths, media and resources are not impacted. The change applies to new meta tag assignments.
Testing: -
Risk rating: Low
Custom design monorepo override improvement
Overview: An update improves how custom CSS can be implemented within designs. The Learning Suite designs are very complex with custom CSS previously required to be written into .json files. The update allows now to write custom CSS directly into familiar .css file.
Benefits and Use Cases: Simplifies how the custom CSS is handled with the new framework (react). This in turn allows greater flexibility and reduces risk of errors.
Audience: All users
Setup & Access: Not required
Considerations & Limitations: None
Testing: This update is quite technical and would only apply to customers with custom design changes: Go to any Learning Suite page (E.g. Configuration manager), view the page source, and see that there is ucl.custom.css file embedded with the correct URL.
Risk rating: Low
Security findings (Other)
Overview: There has been one update with Innovation Pack 23 to reduce a potential security risk.
Authentication and Session Management when changing password for AWS systems
Overview: An update was made to session handling to deauthenticate all active browser sessions if a user changes their password. This potential risk was identified on AWS systems using Kubernetes architecture when a user had multiple browser sessions open.
Benefits and Use Cases: Ensures greater security and prevents potential account hijacking. Updating a password in one session would end all active sessions in other browsers.
Audience: All users
Setup & Access: No configuration required
Considerations & Limitations: This risk was specific to AWS hosted systems on the Kubernetes architecture.
Testing: To test log into the LMS with the same user on different browsers. Then change the password in one browser and refresh the other browsers to check if the session ends.
Risk rating: Low
